In our hyper-connected world, trusting anything by default whether a user or device can be a huge risk. That’s why the zero trust security model has emerged as the no-nonsense alternative: never trust, always verify. This guide unpacks zero trust, explores how to implement it step-by-step, shares insider tips, and highlights real-world success stories. By the end, you’ll see how this shift protects modern networks and why it’s becoming the gold standard in cybersecurity.

What is Zero Trust Security?
Traditional security once depended on the idea of trusted internal networks and firewalls. But that approach crumbles with cloud services, remote work, and mobile devices. Zero trust security model throws away implicit trust, applying continuous authentication, least-privilege access, and microsegmentation, well every single time a user or device tries to access anything. It’s a fundamental shift: no one gets in without earning that access, always.
Why Zero Trust Matters Now
Today’s attackers aren’t just knocking, they’re already inside. Zero trust assumes compromises will happen and minimizes the damage they can cause. It restricts lateral movement within systems, continuously monitors activity, and ensures each session is verified. The result? A dramatically smaller attack surface.
Core Principles of Zero Trust
Three pillars define this model:
- Verify Explicitly: authenticate and authorize using every data point: user identity, device health, location, behavior.
- Use Least-Privilege Access: users and apps only get the minimal permissions they need, for as long as they need them.
- Assume Breach: use microsegmentation, encryption, and analytics to detect early and contain damage.
Understanding the Five Pillars
The US Cybersecurity & Infrastructure Security Agency (CISA) breaks zero trust into five pillars: Identity, Device, Network/Environment, Application/Data, and Automation/Orchestration. Together, these cover all angles from verifying who you are to continuously monitoring behavior.
eady to Implement? Follow These Steps
Assess & Map Assets
Start by listing users, devices, apps, and workflows. Define your protect surface, the crown jewels such as customer data, servers, and critical apps.
Strengthen Identity Management
Use strong authentication (MFA, SSO) and IAM tools. Enforce role-based access with configurable time limits.
Segment Networks & Apps
Divide your infrastructure into tiny zones that only allow necessary communication. This microsegmentation stops lateral spread.
Verify Device Posture
Check if devices are updated, patched, and safe at every access. Devices must continuously prove they’re secure.
Encrypt and Protect Data
Always encrypt data at rest and in transit, and add DLP tools for sensitive info. Fines from breaches make encryption non-negotiable.
Continuous Monitoring & Adaptive Policies
Log every request/event and use analytics to flag risky behavior. Create rules that throttle or block access when things look odd.
Plan for Breach
Assume a breach is inevitable. Build alerts, automation, and incident response into your security stack from the start.
What to Do & Avoid
Do:
- Start small with a clear asset scope
- Use phased rollouts with automation
- Educate users on why MFA and device checks matter
Avoid:
- Trying to boile the ocean, too broad is overwhelming
- Relying on a single vendor, mix IAM, endpoint, network tools
- Turning off MFA for convenience, it weakens your best defense
Top Secret Tricks Nobody Tells You
- Begin with identity-first segmentation; roll out network segmentation later
- Use Just-In-Time (JIT) access for admins, but only elevate privileges when absolutely needed
- Automate logs and alerts through SIEM or XDR tools
- Build a “Zero Trust story” for hires, even walk them through how it keeps database, tools, and digital assets airtight
eal-World Success Stories
Google’s BeyondCorp transformed internal access policies so employees no longer need VPN, every request gets validated. For global firms like Surespan, zero-trust ensures remote collaboration isn’t slowed by flaky VPNs, and sensitive design files stay secure even across borders.
Common Implementation Challenges
- Legacy Systems often don’t play nice with dynamic policies
- User Pushback: new MFA prompts can annoy users
- Costs: zero-trust involves tools and automation
- Complexity: requires mapping workflows and permissions meticulously. Use a phased approach: pilot one department, refine, then scale up gradually.
Why Adoption Matters
As remote and hybrid work becomes the norm, threats advance faster than traditional gatekeepers can respond. Zero trust offers a proactive defense which embedding vigilance and control across every access point. It aligns with global compliance needs (GDPR, HIPAA, PCI), so architects can rest easier knowing policies meet regulatory demands
Tools & Technologies You’ll Need
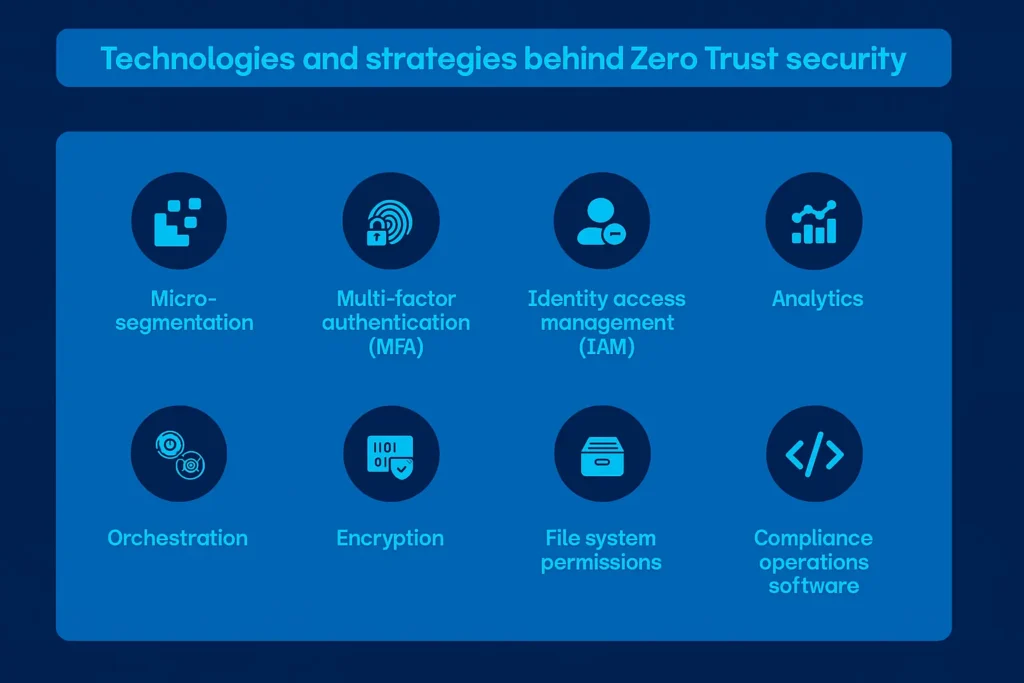
- IAM & MFA: Azure AD, Okta, AWS IAM
- Endpoint Security: EDR platforms like SentinelOne or CrowdStrike
- Network Segmentation: NAC or ZTNA tools
- Encryption & DLP: Use TLS everywhere, add DLP for sensitive data
- Monitoring & Automation: SIEM (Splunk, Elastic) or XDR with behavior analytics
Continuing Zero Trust Over Time
Zero trust isn’t “set and forget.” Patch devices regularly, review access logs, run simulations, and update policies as roles and needs evolve. This model shines most when integrated into daily devops sprints, audits, and training.
Final Thoughts & Call to Action
Zero-trust isn’t just a buzzword, it’s the essential model for modern digital security. By verifying identity and device posture every step of the way, and granting least privilege access, you stay one step ahead of attackers. Start small, automate key steps, and grow your zero trust posture from the ground up. Pairing this approach with hands-on learning like a Best free coding course that are even better than your college degree or building backend demos from Top Backend Project Ideas: Perfect Picks for Portfolios & Resume puts your security career on solid footing.
And of course, just because you build it doesn’t mean you won’t need it, know What to Do If Your Data Is on the Dark Web (Step-by‑Step Guide) as part of a well-rounded security plan.
Ready to lock it down? Choose your first asset to protect today, add MFA, segment your network, and continuously monitor. Zero trust isn’t perfect, but it’s infinitely stronger than blind trust. Let defender confidence become your new baseline.
A zero trust security model assumes no trust—continuous verification of users, devices, and applications before granting access, regardless of network location. This minimizes breach impact and enforces least-privilege.
Start by mapping critical assets, then secure identities with MFA/SSO, segment networks, verify device posture, encrypt data, monitor access, and automate response using tools like IAM and microsegmentation.
Zero Trust relies on continuous verification, least-privilege access, and microsegmentation. Every access request is authenticated, authorized, and encrypted to restrict lateral movement.
Avoid jumping in too broadly. Don’t neglect stakeholder buy-in or underestimate costs. Don’t disable MFA for convenience. Instead, phase implementation and provide training.
Implementation time varies. A basic rollout might take a few months; full maturity, especially in large orgs, can take 12–18 months depending on asset scope and automation readiness.